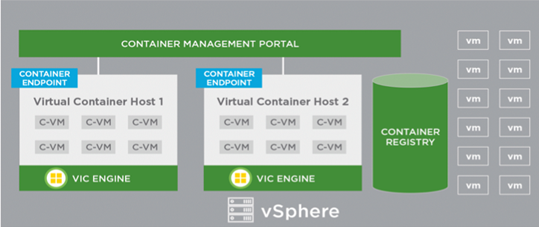
One of the main innovations in VMware Integrated Containers 1.3 (VIC) is the extended plugin for vSphere Client UI (html5) with which you can configure and run the VMware Container Host (VCH). This plugin depends on the correct SSL configuration in vCenter. And here the river theme appears, what is the correct configuration? As it turns out, everyone who has generated a certificate from VMCA signed by Root CA (aka custom certificate) has an almost good configuration. Where the problem arises, I will describe below.

2018/02/09
by Piotr Pisz
0 comments