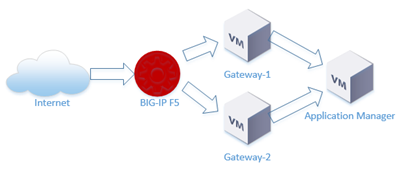
Preparation of fault-tolerant installation of Horizon Workspace 1.8, required at the beginning the creation of the database cluster, built on the basis of pgPool and vPostgres In the next step We prepare more gateway-va machines, and build the appropriate configuration of balancing traffic between them using the F5 BIG-IP. In this case, F5 is also responsible for the whole sphere of security (described in this post comes from our lab and is based on two F5 BIG-IP VE (ie fully virtualized)). If you do not have F5 LTM, you can use the Proxy-HA balancing, and security to pass on to other layers (eg, Trend Micro Deep Security ).
As shown in the diagram, traffic from the Internet to the portal through F5 is directed to two gateways, and upon movement from inside (Intranet), NAT is performed directly to the FQDN address. This solution works without problems (and its configuration poses no problem), but before you proceed to perform the following steps, make sure that your DNS configuration (including the FQDN of the gateway-va) are correct .
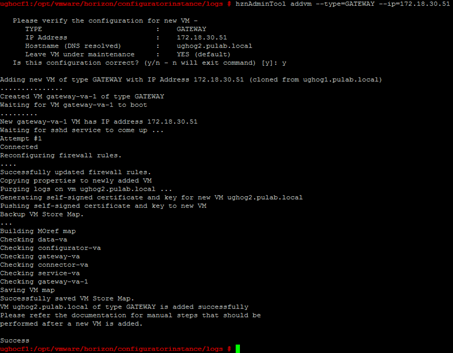
Generate new gateway machine-va is very easy, just log in via ssh (as root) to the machine configurator-va, and issue the command:
hznAdminTool addvm-type = GATEWAY-ip = 172.18.60.144 (IP = address of the new machine based on a new DNS record)
As you can see, part of the process is to generate an SSL certificate for the machine. This is done exactly at the same script , which can themselves be manipulated by hand (to generate and distribute keys and certificates to the machines). The entire process is sealed in a few minutes (for the two new gateway machines). As the load increases, we add another machine, the new always arises as a clone of the last generated.
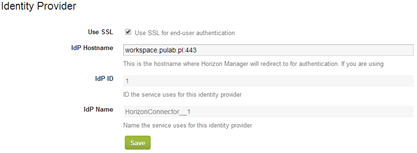
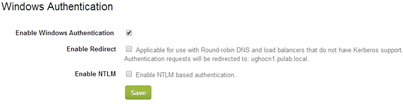
We must also remember that if you access from the Internet, the Identity Provider (IdP) must also be reachable from the Internet. Which means that we have two methods to authenticate. Traditional method (the default installation of Horizon Workspace) where gateway-va is also IdP (then disable “Enable Redirect ‘ in configurator-va):
Or other method in which we generate additional machine configurator-va, which is IdP (turn on “Enable Redirect ‘) which must have a valid FQDN address (online) and be available to the gateway through NAT (does not have to be really exposed to the Internet ). As you can see, the exact rethinking architecture of Horizon Workspace is crucial for the future, the proper functioning of the whole.
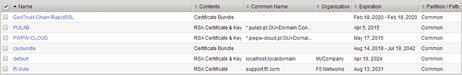
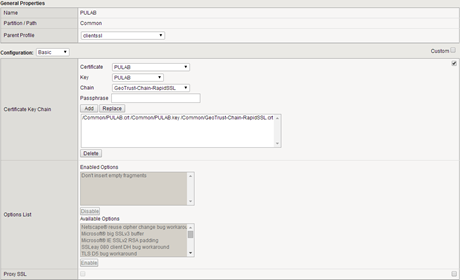
At this point, you can configure F5. In the first step we import (System-> File Management-> SSL Certificate letter) key and SSL certificates of our domain (in this case a wildcard certificate ) and create a new SSL profile:
In our LAB we using F5 version 11.5.1 (build 2.0.121), is the latest version at this moment, a lot of things have changed in it when it comes to the philosophy of some items. Therefore, as shown above, the certificate chain it is best to import separately (in relation to the certificate). Create SSL profile in the “Local trafic-> Profiles-> SSL”:
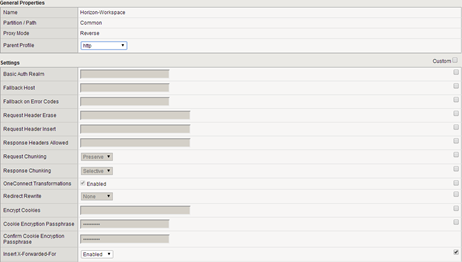
Under the “Local trafic-> Polices-> Services-> HTTP” create a HTTP profile with enabled X-forwared-For (very important):
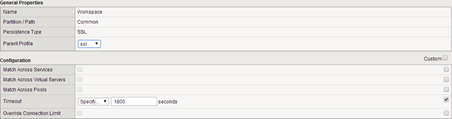
Under the “Local traffic-> Profiles-> Persistence” create a profile named Workspace in which lengthen the waiting time for an SSL session:
Under the “Local Traffic-> Nodes” add our new machines gateway-va:
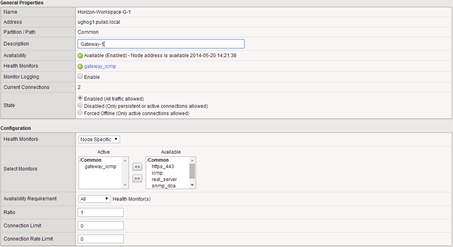
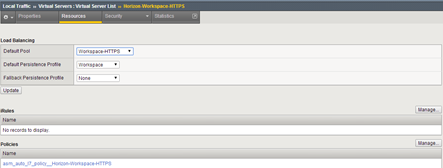
Under the “Local trafic-> Pools” create a pool of our machines:
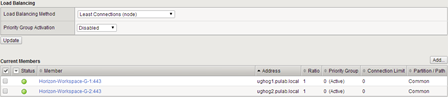
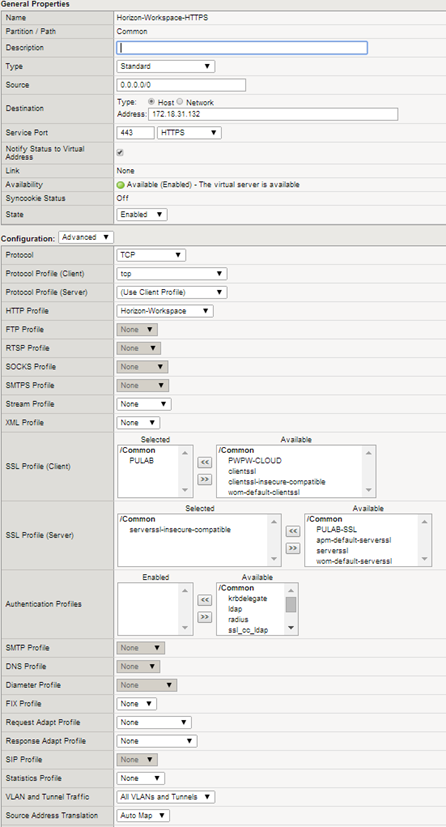
The last step is to create a virtual server with the following parameters:
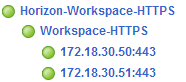
In the end, we get a proper load balancing for Horizon Workspace:
In the next post I will present balancing traffic to Horizon View Connection Manager servers and the whole circuit of the Horizon Workspace (access to the View machine by BLAST protocol directly from the Workspace portal).
Was this information is helpful? Tell me, please leave a comment!