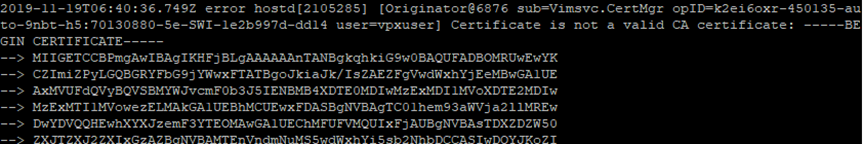
The current version of vCenter 6.7U3 brought with it an interesting change, as we can read here, all CA certificates in trusted store must have the “X509v3 Basic Constraints: CA: TRUE” flag set. Lack of this flag in any certificate basically blocks all operations on certificates, the error “Certificate is not valid CA certificate” appears. Today, on the example of the problem with refreshing CA certificates at the host level, I will show you how to deal with it. Generally, as I wrote in this post, the vCenter CA certificate store should be in order, the mess brings only problems.
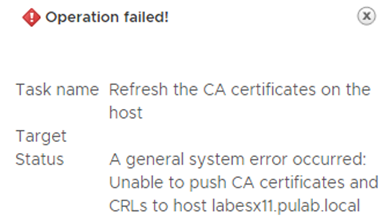
In preparation for refreshing the vCenter certificate (machine cert), I decided to upload new CA certificates to the trusted store and send them to all ESXi hosts. The procedure stopped very quickly with the message:
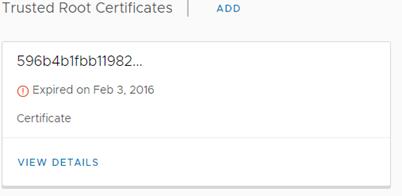
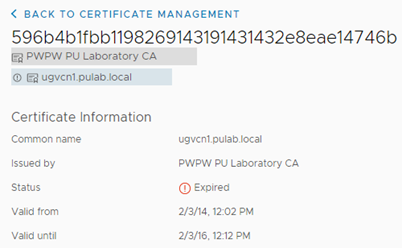
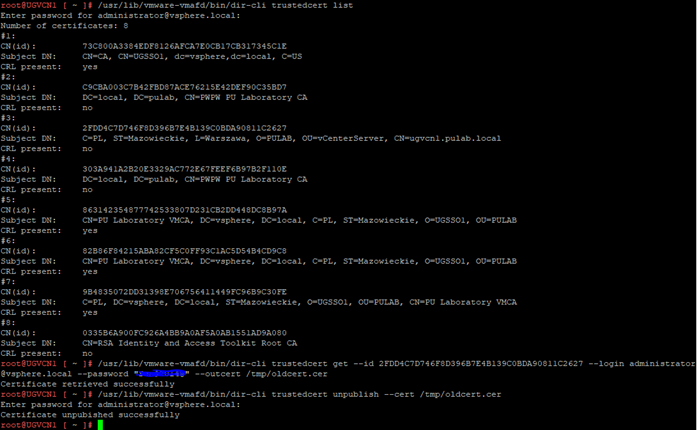
Immediately after the message “Certificate is not valid CA certificate” is the listed certificate, and it was not one of the CA certificates that I added. As it turned out, after checking the contents of the trusted store, there was a old expired vCenter certificate.
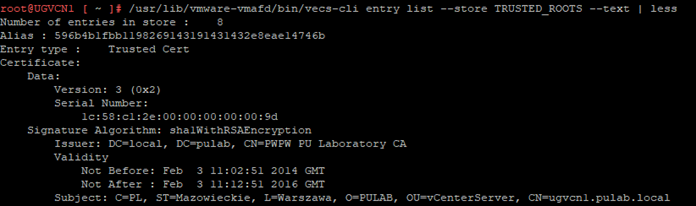
We used certificates signed by external CA for vCenter up to a point, later we switched to certificates generated by VMCA signed by MSCA. This certificate is a remnant of migration and its presence is definitely not in line with 6.7U3 policy. To solve the problem, the vCenter certificate should be removed from the trusted store, we do it from the vCenter shell. We list the contents of the trusted store:
We list the certificates to check the correct certificate ID, then export the certificate we are interested in and finally remove it from VMDIR:
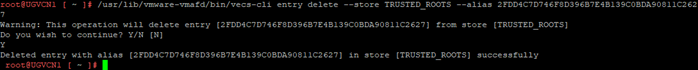
Finally, we remove this certificate from VECS:
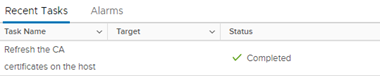
All steps are carried out in accordance with this KB, as we have deleted the certificate that was not used, we do not need to perform any restart. We can immediately refresh the CA certificates on ESXi: