Building at home test environment often start with a very basic configuration. A small computer, NAS and router from your ISP are perfectly adequate. From the time when knowledge and skills grow, so are the demands that we make against the environment also grow. As we know, have fun with virtualization sooner or later will lead us to the point where we find that several tagged VLAN that is what we would like to have. In this post I will present what I had initial configuration and how it expanded with the behavior of existing functionality. The idea of what I guided mainly to get rid of the ISP router as the primary device on the network, and the introduction of tagged network (VLAN X) with maintaining existing non tagged network (VLAN 1). Described configuration applies to specific hardware, but it can be successfully used with the equipment of other suppliers (eg. TP-Link + Netgear).
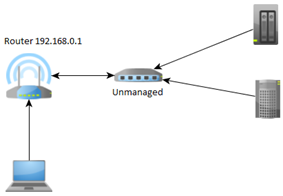
I have a fully functional lab with ESXi and vCenter, entirely built based on the access network (VLAN 1). That’s why I could not completely get rid of this network (re-addressing is not an option), especially since all my home infrastructure is integrated with services running there (eg. DNS server). Old configuration consisted of a IPS router and unmanaged L2 switch.
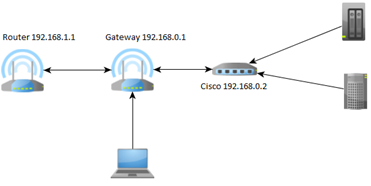
In the target configuration I wanted to have L3 switch with full support for VLANs and routing between them. After a long figuring out what to do and looking over the price of the equipment decided to buy Cisco SG-300-10 switch. Only 10 ports, but it is the equipment of the highest quality and without any compromises (finally). An additional objective as I mentioned was the desire to eliminate the ISP router from advanced configuration. The ISP hardware can do very little or almost nothing and for inclusion the L3 switch need a bit more than just port forwarding. So I had to introduce an additional element, the old router D-Link DIR-300 running DD-WRT functioning as a gateway between the ISP router and L3 switch. Whole looks like this:
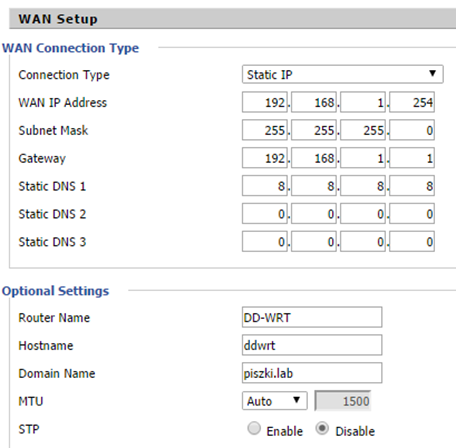
Now I will show you how to set things up, I did a parallel configuration next to the existing, therefore begin with the preparation of DD-WRT (can connect separate WiFi and everything calmly configurable). As the output addressing is 192.168.0.0 additional VLAN will function as a network 192.168.10.0 (Tag 10) 192.168.20.0 (Tag 20) and so on to 90. Nine additional networks is already a major resource in the home lab. Log in to the DD-WRT and configure the basic parameters of the router. WAN address is a fixed IP address of the new IPS router subnet 192.168.1.0
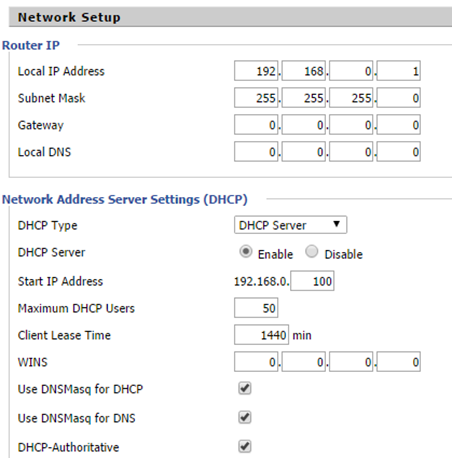
Gateway address for the LAN is the old address of the ISP router from the 192.168.0.0 network, in addition to start the DHCP server from which the Cisco switch will get its own IP address.
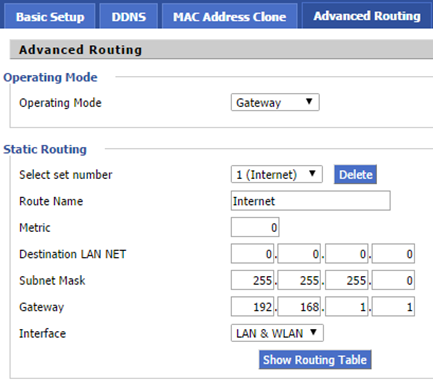
And now, most importantly, devices in the internal network get access to the Internet (external network). We need to configure additional static route (basic supports 192.168.0.0) network other than the internal router leading to the ISP. Gateway is a new ISP router address 192.168.1.1 after migration (described at the end).
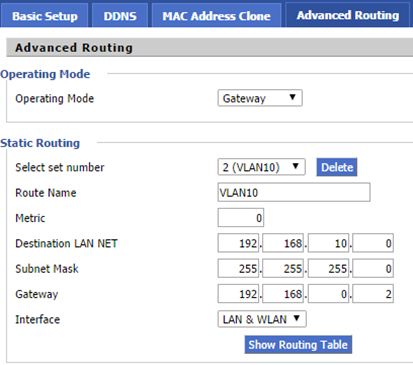
In addition, for each vlan network we need to do a separate static route indicating the address of Cisco to which it is hooked gateway (D-Link). Without this traffic from the external network will not return to the internal.
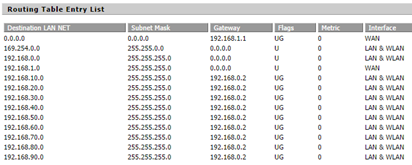
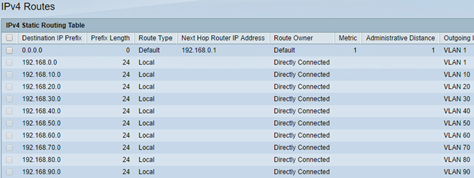
Full route table.
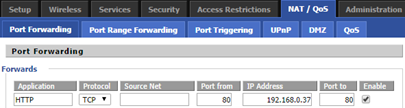
Of course, for services such as port forwarding we are doing configuration at the level of DD-WRT (Gateway), at the ISP (Router) such a redirection must be removed (not only will not work, but block the communication).
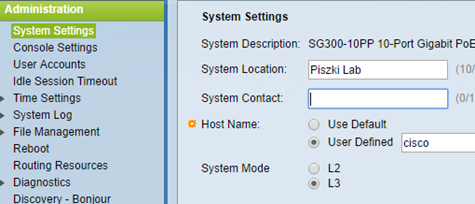
And all this on the DD-WRT. We will now proceed to Cisco which is connected to the DD-WRT, Cisco gets the address from the DHCP log with login cisco and password cisco. In the first step we have to switch the mode from L2 to L3 (switch will restart a previous configuration is erased). Remember that the IP address that the switch downloaded from the DHCP become his primary address (permanent). His change is possible only with the console accessible via serial cable (do not do this via the web or ssh).
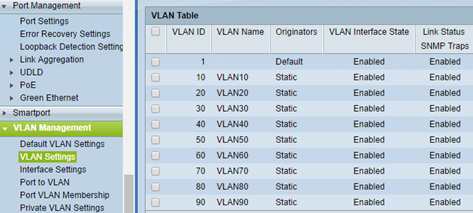
I describe here only the configuration of these parameters, which are related to the topic of the post, in the configuration, you can still have a lot of other things to change. On the VLAN ID set any VLAN, but do not change the default VLAN 1.
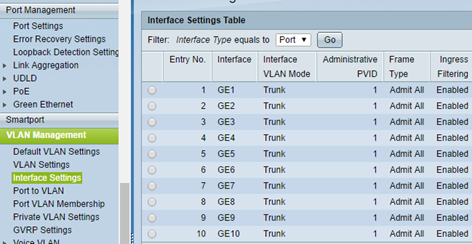
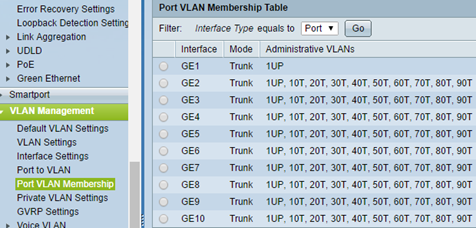
All ports VLAN Mode should be set to Trunk and it does not matter that we will mix settings.
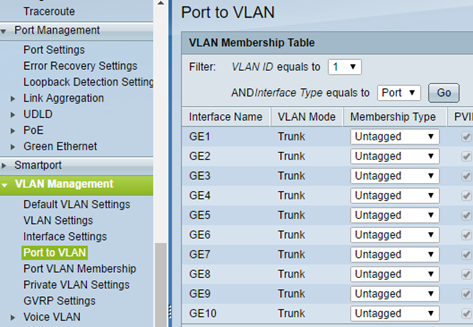
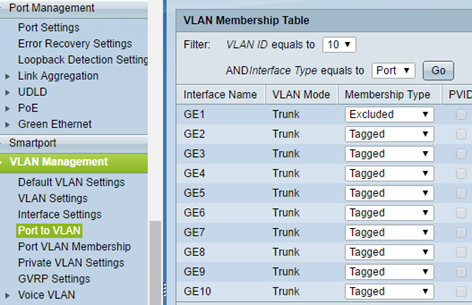
In the Port to VLAN assigns the TAG VLAN to the port. VLAN Membership 1 type is left as an Untagged.
For each additional VLAN ID set Membership Type Tagged as bypassing the port 1 which will be hooked to Gateway (D-Link DIR-300).
So should Port VLAN Membership look like this.
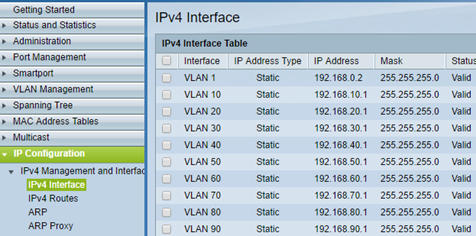
In the IPv4 Interfaces we give IP addresses for each VLAN, these addresses will function as a gateway within the network. For VLAN1 address we set only from console.
In the last step, set routing, Next Hop Router is the internal address from DD-WRT (D-Link). Other networks are routed internally.
At this point, we can save the configuration of Cisco and activate. The process of switching the old network configuration to the new is extremely simple. Repoints ISP router to 192.168.1.1 (remove all port forwarding rules and add DD-WRT to the DMZ). Connect the DD-WRT (WAN port) to the ISP router and all devices (eg. ESXi) repoint to Cisco. Everything should work without problems in the old access network 192.168.0.0 and additionally we ping the VLAN gateways.