On 2015.08.13 premiered Trend Micro Deep Security 9.6 which is now fully compatible with vSphere 6.0 and 6.1.4 NSX. This version brings a lot of news and bug fixes, but if you are holders of vSphere 5.x exactly reads the ReadMe (before doing the upgrade). Trend Micro follows the VMware approach to the vShield Manager. In principle, the use of vShield Manager 5.x in vSphere 6.0 has no sense (in the case of vCloud Suite 6 license – this is not possible). A similar situation exists in the case of Trend Micro Deep Security 9.6. Support the configuration of vSphere 6.0 + vShield Manager 5.4 but this solution does not support … agentless VM protection! If we want our environment to migrate to the latest version and keep agentless security, we need to do to upgrade all components (including vShield -> NSX).
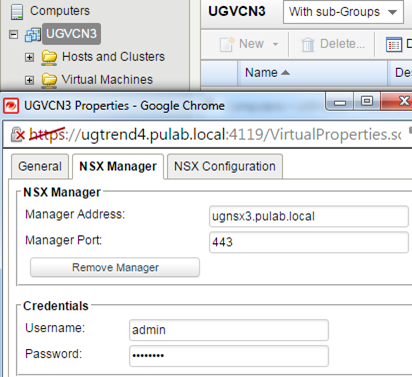
Same configuration of the whole, Deep Security 9.6 with NSX 6.1.4 in vSphere 6.0 environment, is quite simple and can be done in several steps (I assume that everything we have already installed). In the first step we need to set up a connection between Deep Security and the NSX, we do it in the “DSM –> Computers” (if you previously did not do it, in the same place connect to the vCenter). At this point, Deep Security are add in the NSX as Service.
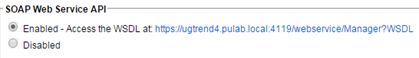
We also need to see the “DSM –> Administration –> Advanced” to enable SOAP API:
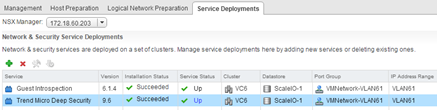
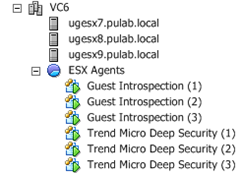
Now we go to the NSX in the section “Installation -> Service Deployments” must install the two services, Guest Introspection and Trend Micro Deep Security.
It is a very simple procedure (click on the plus and go through the wizard). As a result of this operation on our ESXi hosts install a new machine “Guest Introspection”, is the equivalent of vShield App and “Trend Micro Deep Security” (is nothing like DSVA).
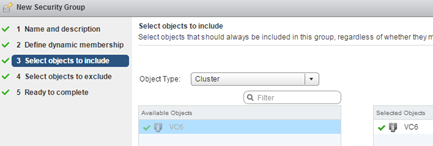
Now we have to connect on NSX the two services, we do it in the Service Composer. In the Security Groups we create our first group (vm protected agentless), add whole cluster of ESXi. The position of the “Define dynamic membership” leave empty, in the “Select objects to exclude” select which machines should not be protected. This is an important observation that when you first turn on the policy, Deep Security automatically activates the machine it covers (it is worth to exclude service machine like DSM).
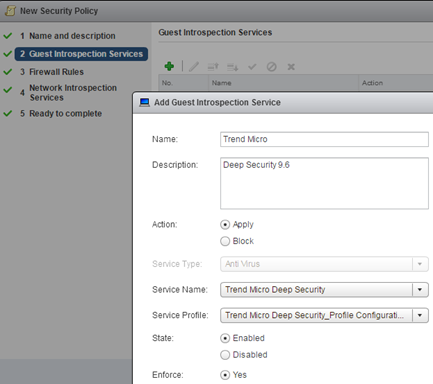
Go to the “Security Polices” and create our new security policy. In the first step we give her name, next add the service “Trend Micro Deep Security”:
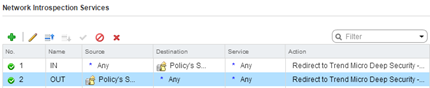
In the “Firewall Rules” nothing to add, then in “Network Services Introspection” create two rules IN and OUT with the following parameters:
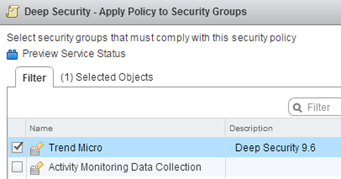
In the final step we apply Security Policy to Security Group:
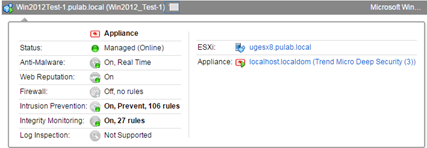
Now we have to wait a little longer, Trend Micro Deep Security automatically activates the machine of the NSX security policy. After this process, we can proceed to distribute the Deep Security policies to machines (NSX security policy is something other than Deep Security policy).
The combination of the VMware NSX and Trend Micro Deep Security provides many new opportunities, auto-tagging and react to events (I will write about this soon). Support for vCenter 6.0 allows VMware to migrate vSphere 5.5 up with full protection without agents.