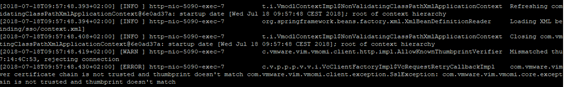
In our configuration (as a past after vSphere 5.5) we have a vCenter server with external PSC. When testing vSAN, we decided to join to the VMware CEIP program due to the extension of vSAN cluster monitoring. Unfortunately, the connection turned out to be unsuccessful. After a long search for the cause, it turned out that the error (as usual) is in the certificate. In the virgo log of the vSphere client (flex and html5), the following errors were shown (Server certificate chain is not trusted and thumbprint does not match):
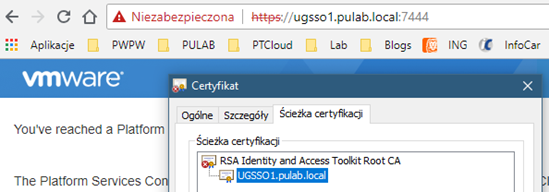
I will add that in case of vCenter and PSC we use certificates signed by our own CA and VM CA functions as SubCA. After checking, it turned out to our surprise that the main SSO certificate is signed by the RSA Identity and Access Toolkit Root CA. In order not to make a big fuss, we decided not to regenerate this certificate, but only to check if RSA Root CA is present in the trusted key store in vCenter.
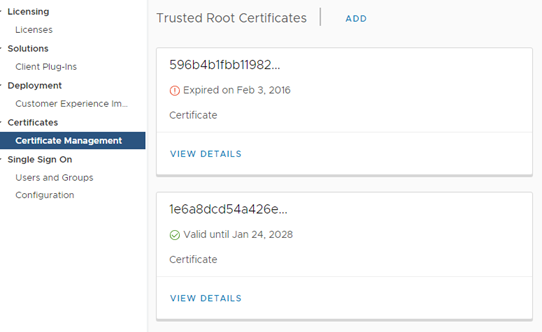
It turned out that not (and not only him), fortunately, it was enough to export the appropriate certificate and add it from the vSphere UI client level in the Administration -> Certificate Management section.
Thanks to this simple trick we managed to solve the problem.