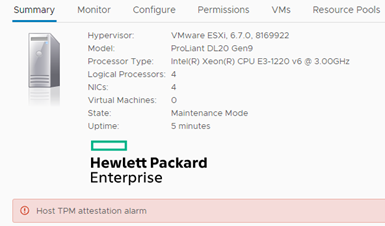
TMP is a system that stores information that allows the authentication of the hardware platform. This information is certificates, passwords and cryptographic keys. There are many applications for this system, for example support for BitLocker in Windows. In the case of vSphere, support for TPM 2.0 appeared in version 6.7 (in the lower versions, e.g. 6.5, the layout of TPM 2.0 will not be visible). Does it affect us and how can we use the TPM 2.0? If our server is equipped with a TPM system that is in UEFI enabled (only UEFI is supported, there is no support in the traditional BIOS) and visible to the server, then an interesting message will appear in ESXi:
ESXi 6.7 uses the Secure Boot function in conjunction with the TPM 2.0 system. This means that by starting ESXi, we guarantee that the launched software is digitally verified and has not changed. Why is this important? Nowadays, at SDS times, most servers are run from an internal SD card or USB device. In most servers, this card is available without opening the case (Dell). The card can be removed, copied, made a few changes and put in again. TPM gives us information if the server was not manipulated at reboot. Abstraction? Man in the Middle is still the most popular attack in the world. In this article I will show how to set up the whole this using the example of HP DL20 Gen9 server (which came into my lab and I will write a separate article soon). At the beginning I will use graphics from the VMware website showing the ESXi boot sequence.
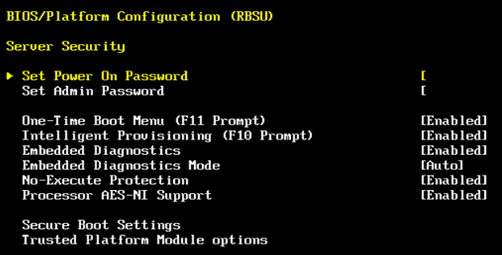
We turn on the power, the host loads UEFI which checks the Boot Loader, ESXi starts. VMKBoot communicates with TPM, information about the host is sent to vCenter to check if everything is OK. In detail, this aspect is discussed in this article. And here is the restriction, a single host, no vCenter or vCenter running on it, can not be checked in this sequence. Thus, always in this situation the above message will appear about the lack of certification. The configuration starts with the server, in the case of HP we enter UEFI -> RBSU -> Server Security:
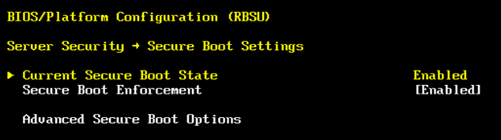
At this point, we can first turn off the TPM or disable TPM visibility for the host, which of course closes the topic. Otherwise, we enable the TPM and its visibility for the host. In addition, we enable Secure Boot and restart the server.
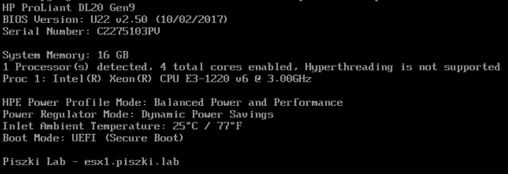
When displaying POST messages, it is clearly visible that UEFI Secure Boot is enabled.
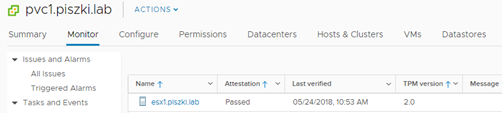
The configuration for TPM is created when you add the host to vCenter, if you already have a host in Inventory then you must perform the Disconnect / Connect operation. During it, shortcuts (hashes) are generated which are saved in TPM and in vCenter. During the next restart the host will compare the shortcuts and if everything is ok then in the section vCenter -> Monitor -> Security we will see the information that the host has passed the verification correctly.
And that’s basically enough, the use of this mechanism increases the safety of the environment. In this article, you will find questions and answers about TPM in vSphere 6.7. It is also worth adding that the inclusion of TPM in ESXi 6.7 means that we can use TPM in virtual machines (vTPM). As we can write a lot of information in the system itself, security can be extended to both hypervisor and virtual machines. The topic is developmental and I think VMware will continue this project.



One Comment
Leave a reply →