Edit 2014.04.15: Finally, I created a script to generate a proper certificate for (almost) any SSL (VMware) service. It works very well with LogInsight! You can find it here. You do not have to perform the steps described below! :)
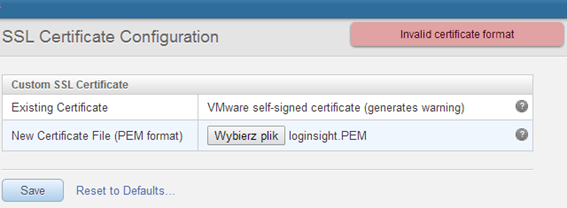
Today I tried to replace the SSL certificate on a freshly installed instance of VMware Log Insight 1.5. Whatever I did, however, would not generate a key pair + certificate (does not matter whether it was openssl or Microsoft CA), always display the message “Invalid certificate format”:
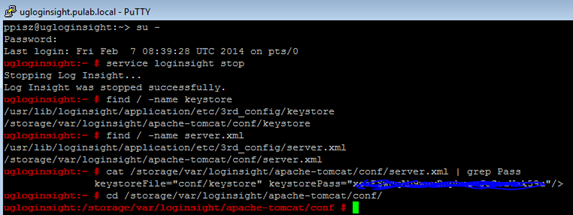
And it is not a separate case, I have three instances of Log Insight, and each behaves in exactly the same way. I searched the Internet, but I found very little and nothing that would solve my problem. After a few lost hours, I decided to solve this problem, as it has already done , picking the console. At the beginning we prepare ourselves in our CA (in my case Microsoft Server 2008R2 CA) parcel (pfx, or PKCS12) containing the CA certificate, RSA key and server certificate. Copy file in to our machine Log Insight. In the virtual machine console create a user in the group “wheel”, log in using putty and execute a series of commands (as root), starting from stop service loginsight.
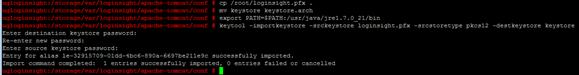
We already have a keystore file location and password to him and to the private key. In the next steps we substitute our own key and certificates. Using PKCS12 format has the advantage that it does not need to generate a private key in the keystore, it will be installed from our pfx file. If we carry out the process using openssl, it is best to also prepare the file in PKCS12 format, otherwise awaits us classical path (key generation, request and finally upload the certificate).
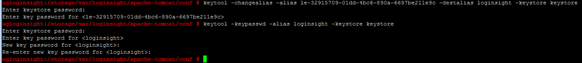
Please note, the password for the key in pfx file was different than the keystore, so the last command, change the key password, so that was the same as the keystore file! We change it to the correct alias of the certificate:
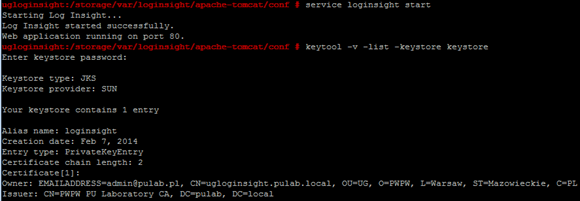
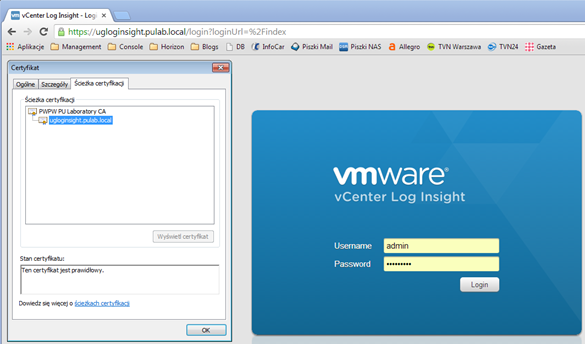
At the very end we start loginsight service and look forward to our new, wonderful, certificate:
Of course, this method is not officially supported, but it works very well. Long analyzed the logs in a virtual machine, I have not found the cause for which I could not import the certificate and key by the web interface. Exactly the same certificate + key pair, who did not want to import the web, acted after a manual import. The problem probably lies somewhere in the application code and hopefully that will eventually be corrected (also appeared in Log Insight 1.0). I hope I helped![]()
Was this information is helpful? Tell me, please leave a comment!