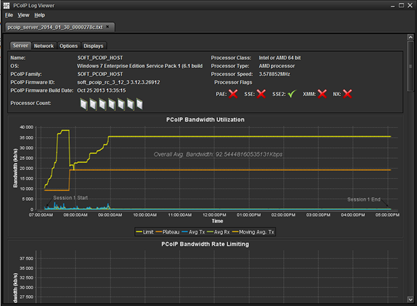
In our laboratory, we have a pretty good environment, except unfortunately the network. It just happened that the network is administered by someone else and to Lab get garbage. Old routers, switches etc even older. etc.. At the moment in which our entire department went on thin terminals , we began to feel the wild fluctuations that ultimately brought to the widespread, quite accidentally, unfasten the PCoIP session. Diagnosis of the problem is very difficult, it often happened that the one terminal run for hours without a problem, and the outlet next door, could not work, restart every minute session. The session logs often appeared the message: No PCoIP date received in the past 3 seconds (to peer connection might be lost). And in the course of intensive work and a virtual machine!
At this point I really want to commend the author of the PVoIP Log Viewer , brilliant tool, literally drags to light all the parameters of our PCoIP session.