One of the novelties in Horizon View 5.3 is the ability to use Windows Server 2008R2 as a workstation. This facility was established primarily for the license , the manner of licensing Windows 7 and other desktop systems in virtual environments, it is not optimal from a cost point of view (in the implementation of Horizon View). Therefore, please note that we can only license to use in such a configuration, it is invariably Datacenter. The documentation is written is true that other licenses have not been tested (that may work), but the use of a standard license on a massive scale is not viable completely. Currently, Windows Server 2012R2 is not officially supported, but that is licensed in the same way, it is expected that soon, and this configuration will be available.
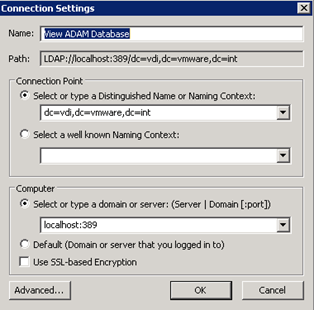
Preparation for the operation of this configuration is quite simple, at the beginning we need to configure our Horizon View Connection Server. Start the ADSI Editor (Start Menu -> Administrative Tools -> ADSI Edit). Then connect to the local instance of ADAM server :