Before writing this post I made a little research. I came out to me that it is not so easy to arrange remote access through the web browser to your own workstation. There are various solutions, for the most demanding installation of the server and the client. The closest solution to this which I will describe here, is probably “Microsoft Remote Desktop Web Access”, but it is a feature of Microsoft Server. And now we have a premiered VMware Horizon 6 with View, and with it a novelty, Horizon View HTML Access. Under this name hides the BLAST protocol, which until now has been part of Horizon View Connection Server and which allow holders of View infrastructure comfortable working on workstations from anywhere via a web browser. Today has been separated out (View construction has become more modular), installation and configuration is not simple (but also without exaggeration), but its completion will allow us, for free, enjoy remote access to the desktop. I write it for free, of course, you first need to download Horizon 6 with View the 60 day license, but Direct Connect itself does not require installed and valid license. Besides, VMware has a very liberal attitude to the “Home Lab” and does not make the problems people gaining experience in the field of their products.
The whole procedure is in three steps and is as follows:
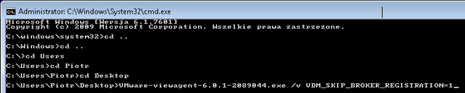
In the first step we need to download and install Horizon View Agent version 32 or 64 bit (depending on your system). Of course, download the add-on Horizon View HTML Access and View Agent Direct Connect (32 or 64 bit). The agent must be installed from the command line (as administrator) with the parameter VDM_SKIP_BROKER_REGISTRATION = 1 (Note: we will not use this machine with a View Connection Server):
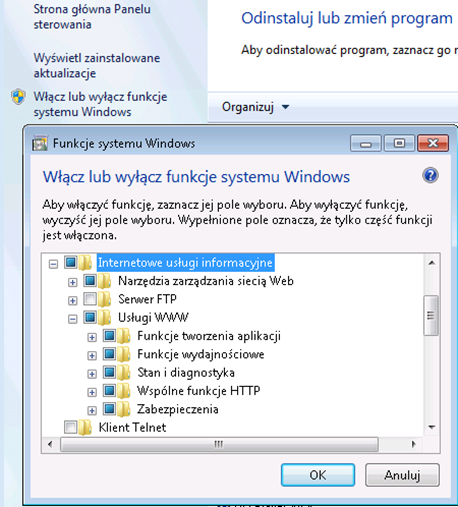
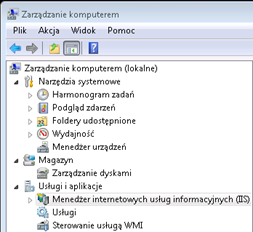
View Agent Direct Connect install as Administrator with no parameters on the default port 443 (this is not mandatory). In the next step, we need to install and configure IIS, this is done very simply. In the Control Panel, select “Programs and Features”, then “Turn on or off Windows features” (depending, of course, whether it is Windows 7 or 8, here is the example for Windows 7 32-bit):
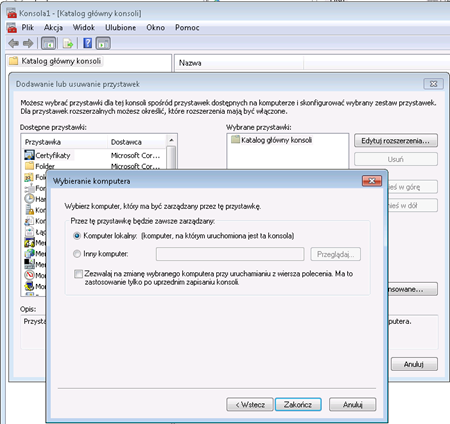
Now we have to see if we have in the system any certificate issued for the computer. We can do this by running mmc snap-ins console (in the start menu, run: mmc) and add “Certificates” snap-in:
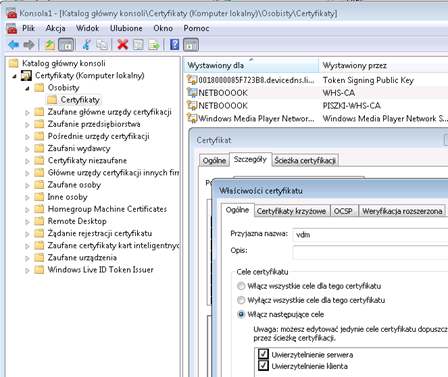
SSL certificate can be anything, as long supported the extension “server authentication” and had a friendly name vdm (add it themselves). This certificate will be used by the web server to display the console of your computer over HTTPS. In the absence of a certificate, you must generate and import it. Here I can only recommend my script CA (requires Linux) or find appropriate tutorial over Internet (or purchase it (example) on the RapidSSL).
In the last step we need to unpack the Horizon View HTML Access (portal.war). Change its name to portal.zip and unpack its contents to c:\inetpub\wwwroot\website\portal (directory “portal” must create yourself). Using as example Notepad, create a file c:\inetpub\wwwroot\Default.htm with content:
<HEAD>
<meta HTTP-EQUIV=”REFRESH” content=”0; url=https://IP or DNS of your workstation/portal/webclient/index.html”>
</HEAD>
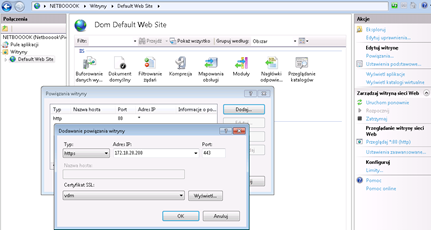
Click on the “Default Web Site” and right in the “Binding”. We are doing a new bind, port 443 to the IP address of your computer (you can check it on the command line ipconfig) with our certificate vdm. I suggest you to immediately remove the default binding on port 80:
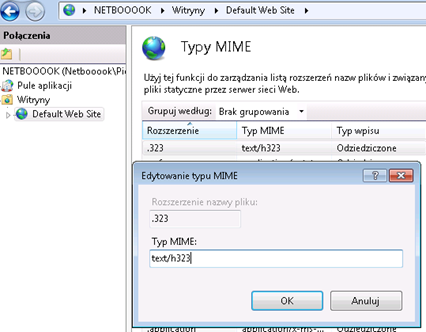
Then add (if you do not have), a new MIME type:
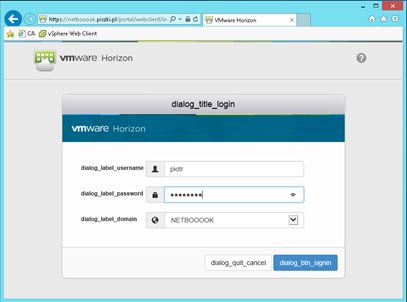
And that’s basically everything. Just remember that if your computer has turned on “Windows Firewall”, View Agent and Direct Connect will create and enable appropriate rules, port 443 is disabled by default (rule “World Wide Web Services”) and must be manually turn on. At the end the safety issues. First, port can be any, as long as he was consistent with IIS and Direct Connect (eg. 8443). On the portal, log in local desktop username and password :
After logging in, select your computer and go to the console (main screen is locked, as is the case for example using RDP). The connection is encrypted, IIS, and the portal are only responsible for the authentication and redirect the port on which the BLAST server is running. If you regularly update your computer, such a solution is quite safe. But you know, evil is always lurking and better play in the security on the firewall, permitted only one IP address (eg. from work). The end result looks like (screen size is dynamically adjusted to the size of the browser window) this:
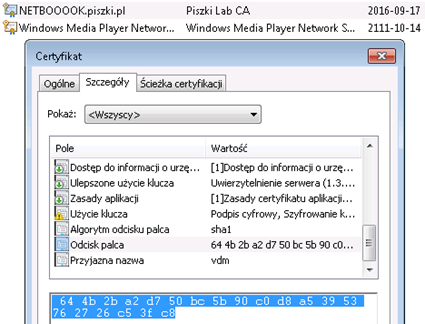
The speed of operation is comparable to the RDP (ie, no jams, etc.). As an addition I will describe what to do when we have our own domain and certificate signed by a CA. Replacing the certificate in IIS takes place on the same principle, import certificate (note: the “mark key as exportable” should be selected), give it a friendly name vdm and we bind it on port 443 on the IIS console. BLAST server implementing real connection and is completely separate from the IIS and certificate replacement looks different. In the same snap-in mmc console (or Control Panel> Internet-Options> Content-> SSL Certificates) in the properties of our SSL display and remember Certificate Thumbprint (fingerprint):
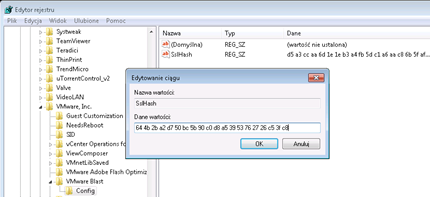
Then run the Registry Editor (regedit) and on the HKEY_LOCAL_MACHINE\SOFTWARE\VMware, Inc.\VMware Blast\Config parameter SslHash paste our Thumbprint:
Then restart the service VMware Blast (or the entire computer if you prefer). If after restart SslHash changed (and log c:\ProgramData\VMware Blast\Blast-Worker.log see the message: Unable to load the private key from the certificate), this means that the private key is not marked as exportable! If everything worked out, we have a coherent certificates in IIS and BLAST. If there are any additional questions I will be glad to answer.



2 Comments
Leave a reply →