For a long time I carried out with the intention to describe this product, in the end there was an appropriate occasion, scored exchange Trend Micro Deep Security 9.0 Support Track, I passed the exam and as of today I am the Trend Micro Certified Security Master :)
Deep Security use of version 8.0 which was installed on the vSphere 5.0, currently we have 9.0 sp1 on vSphere 5.1. In January, comes version 9.5 which will be fully compatible with vSphere 5.5. Currently, our license covers all the modules, but we know that version 9.5 will be extended for another, including those that allow you to scan in terms of security web portals (such as holders of the portal, we are going to test all the new products). Deep Security provides complete protection of the environment in a virtual (and physical), including protection of virtual machines in the “no agent-based.” DSM installation itself is simple . Configuration is intuitive , take a look at it with the ” Best Practice “.
I am a long-time user of this product, with superior experience, I would like to share here some thoughts. I’m also a big fan of this solution but I look at them quite critically on the grounds that quite a long time to stabilized, and at one time gave us a bit of bone. Protection “agent-based” rather not have to explain. In this post I would like to mainly “crack” the protection of agentless around which accumulated some myths. Unfortunately, as always, marketing does not present the whole truth, and some of the details you can learn just … in training.
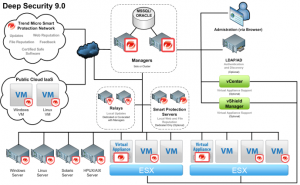
Mechanics of the entire Deep Security introduces himself as follows:
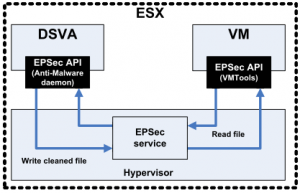
Protection without agents provides DSVA, appliance that must be loaded on each ESXi host. DSVA communicates with the vSphere API through appropriate, therefore, needs to act vShield Manager and the presence on each host ESXi loaded vShield App. A virtual machine must be installed and operating correctly VMware Tools (with driver vShield Driver is not installed by default!). If any of these components does not work, protection is disappearing. Exactly, disappears. Under normal circumstances, everything that is related to the operation of a virtual machine is further filtered by DSVA (just called the driver that you install on each host – filterdriver). Not acting DSVA (eg after reboot the host turns out that it is checked out of the vShield Manager) does not see the machine (offline) and does not interfere with its operation. The rest of the communication is done properly, hence the disappearance of protection. This is a good site, failure of Deep Security Manager and Deep Security Virtual Appliance will never cause that our environment will cease to operate. The downside is that if you want to KEEP protection in the event of a failure, we need to install the Agent.
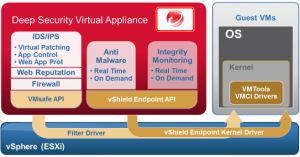
Diagram of DSVA is as follows:
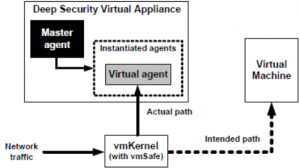
What really is DSVA? It is a Linux machine (we have there full of insight) which are run more instances of agents (for each protected virtual machine). So yes, agentless protection is done using … Agents!
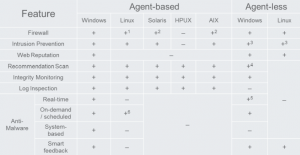
Here we have carefully written out the differences between what is Agent provides a DSVA:
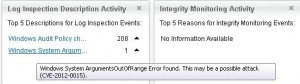
At first glance, you can see the differences between Windows and Linux / Unix. According to the interpretation of Trend Micro, the workload which would have to be made for the expansion of the Unix protection (without agent-based) is not adequate to the obtained profits. Most important, the “virtual patching” (the new nomenclature simply IPS) works perfectly on Linux systems / Unix. It does not work unfortunately Integrity Monitoring (equivalent HIDS). Without an agent will not have a insight into system logs, and the logs can be happening a lot:
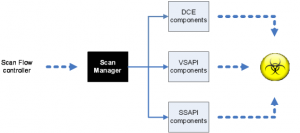
There is a big difference between anti-virus protection provided by DSVA and local Agent. DSVA has “insight” in the machine only through the API, it can scan read files, can scan the contents of the disk, but no insight into what is going on in the memory of the machine:
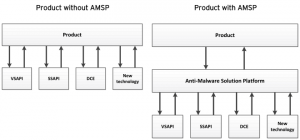
Agent installed locally can do more, use of technology and experience earned over the years with products such as Titanium Security (I mean mainly the protection of Windows). The technology which is used is the AMSP, or Anti-Malware Solution Platform.
AMSP is a modular technology based on plugins, using engines Virus Scanning API (VSAPI), Spyware Scanning API (SSAPI) and the Damage Cleanup Engine (DCE). And that DCE is what distinguishes Agent of DSVA, DCE is directed against threats residing outside the system files (memory, registry and other components such as Layered Service Providers).
And here we come to conclusions. Do agentless protection is a myth? Definitely not! Deep Security, by DSVA provides almost immediate protection of the whole virtual environment. Implementation of the Deep Security can be done in an hour, the initial preparation of the policy and its sending a few minutes. Literally the moment we have enabled virus protection on dozens of machines. Scanning machines for recommendation a few minutes, the inclusion of a recommendation (virtual patching) and redeploy the policies that minute. Within 24 hours, we can perform a full scan machines for anti-malware (depending of course on how much they have). There is no faster method in complex environments, it does not make sense to install the Agent on each machine. We have adopted the principle that agents are installed only where the threat is greatest. Equipment exposed directly to the Internet (website), machinery back-end machines, which must meet certain requirements, such as PCI Commpliance. And at the end of the machine VDI in pools of type Full (yes, no trust).
I hope I explained it pretty clearly about without agent-based protection of virtual machines. :)


5 Comments
Leave a reply →